Have you ever stressed over the safety of your crypto assets? What ways can someone hack you? What steps could you take to make your security framework safer? One of the biggest promises of cryptocurrencies is self-custody. But self-custody also means protecting your funds is your sole responsibility. Since cryptocurrencies are not like insured banks and loosely regulated by governments, getting hacked leaves the users with almost negligible chances to get their funds back. To give you an understanding of the various risks with cryptocurrencies, we have compiled a page that covers various attack vectors that have led to the loss of funds, so you can gain inspiration and take the right steps that would keep your funds safe. This article covers steps you as an individual can take to protect yourself.
Network and Data Safety
Public Wifi are good, they are convenient and most importantly, Free to use. But they are equally loved by the attackers. Public WIFIs open multiple attack options for them like Man-in-the-middle attacks, Fake Wifi, Packet Sniffing, Sidejacking, and Shoulder-surfing attacks on the Wifi users. It’s best to stay away from these public free services.
In case you ever find yourself in a situation where the only option is to use public wifi, here are some things that you can do to keep yourself safe :
- Use VPN: VPN encrypts the connection. So, even if an attacker is able to position themselves in between your connection, the encrypted nature of data packets will cause hindrances to attack you. More on this in the next section.
- Turn off your public Wifi when you do not need it.
- Turning on sharing, changes your firewall settings to allow some communication, which can be a security risk. If you know you won’t need to share files or printers, turn off sharing from the system preferences or Control Panel, depending on your OS.
- Enable the “Always Use HTTPS” option on websites that you visit frequently.
VPNs can be used on any device to maintain your data privacy and avoid eavesdropping or tracking of your activities. A VPN essentially creates an encrypted tunnel that keeps your online activity private and secure, giving you control over your data.
While Phishing scams are the most common in the Web3 world. Somehow, crypto investors still fall for it. Here is the easiest framework to prevent you from falling for it.
- Install Firewall: Both desktop firewalls and network firewalls, when used together, can bolster your security and reduce the chances of a hacker infiltrating your environment.
- Install and keep your Anti-virus updated: Just like you are reading this article to keep yourself updated with the latest security frameworks, the same way your OS and Anti-virus companies send your computer updates regularly. Those are meant to keep your computer updated with the latest attack vectors. Don’t ignore them.
- Don’t click that link: I know you are tempted to click any link, any random person sends you. But be wary, you are better off not clicking it. As a general practice it is safe not to click links to any website on devices that are connected to your crypto assets.
- Social Media: Turn off Auto-downloading of all your communication apps like telegram, Discord, Whatsapp etc. You can do so by finding it in the settings section of the App.
- Bookmark your Dapps: If you are a Web3 native it is likely that you regularly use some Centralized exchanges, DeFi Dapps, and NFT websites. If you are using them regularly why not bookmark them for both convenience and security purposes. This way you will have a lot less probability of falling for phishing scams.
- Security companion: Have a security companion like Wallet Guard to help you protect from known malicious sites and extensions.
- Have unique passwords for all your wallets. 1Password and LastPass are considered two good options for Password Management.
For how much you try, there is a certain level of probability that some malicious actor will somehow get into your security environment. Why not use an antivirus to have your back just like you have a bodyguard and security cameras to have your back in the physical world?
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN.
While it is important to have a strong password, it is also important to add an additional layer of security like an MFA, wherever it’s possible.
Multi-Factor Authentication in Web3 usually happens in four ways:
SMS-based MFA: SMS-based MFA interacts directly with a user’s phone. After receiving a username and password, the site sends the user a unique one-time passcode (OTP) via text message. The user must then enter the OTP back into the application before getting access. Accounts secured by SMS MFA are prone to Identity theft, where someone convinces the telecom service you use they are you.
Never share your contact number publicly. If your phone number is already public, consider getting a new phone number and never sharing the contact number with anyone. Use that contact number for your mobile MFA.
Make sure to contact your network carrier to add an additional layer of protection on your contact number. This can be asking your network carrier to disable sim swap until you personally visit an authenticated store, adding a PIN/Password on the mobile number or some other option that your carrier approves of.
Sim Swap Protection Services: There are sim-swap protection services available like Efani, that guarantee protection against sim swaps and come with an insurance policy against losses due to SIM swaps.
Email-based MFA: Email-based MFA is an extra layer of security to your Private Email account in addition to your email and password for the service.
Email-based MFA considers your private mail to be secured. But in case an attacker is able to compromise your private mail credentials, they can imitate you. Therefore, it is highly recommended to secure your private email. Best ways to protect your private mail is by adding a layer of security with App-based MFA or Hardware-based MFA, both of which are discussed further.
App-based MFA: App-based MFA in Hub is compatible with any app that accepts a QR code or key to pair with your Hub account. This method of authentication is based on the Time-based One-Time Password algorithm. Online services can be hacked by attackers from anywhere in the world. So an attacker knowing about your asset size can target these services and potentially target you specifically. Although, Google Authenticator and Authy App are two good options to use while adding a Multi Factor Authentication layer onto your existing security.
Hardware-based MFA: Hardware-based MFA are by far the safest way to secure with MFA because other options are virtual solutions that can be hacked into by the attackers because of them living on the vast connected space we call the internet. But it is difficult to get access to hardware because of their physical nature. Yubikey and Google Titan Security Key are two good options for Hardware based MFA. Example: Coinbase, a famous crypto centralized exchange has support for hardware-based MFA.
Wallets
If you hold any cryptocurrency, you must hold your assets in a wallet. Wallets are of two types:
- Custodial Wallets
- Non-Custodial Wallets A non-custodial wallet, on the other hand, gives users full control over their private key, and with it sole responsibility for protecting their holdings.
A custodial wallet service (like Coinbase or Nexo) holds on to the private key, so it is responsible for safeguarding a user’s funds.
Self-custody starts with non-custodial wallets, also known as Private Wallets.
Crypto assets sit on the blockchain and are never in your wallet. In contrast to what many think, wallets are aimed at securing your keys and not your assets. There are three types of wallets: Paper Wallets, Software Wallets and Hardware Wallets. But how can you secure each one of them?
First of all, let’s start by addressing the elephant in the room. If you centralize all your assets in one private wallet. It’s highly likely that you are NGMI (Never Gonna Make It). It is always best to distribute your assets into multiple wallets. Now, back to types of wallets and how to secure each one of them.
Paper wallets were generation one of wallets. A paper wallet is a printed piece of paper containing keys and QR codes used to facilitate your cryptocurrency transactions. Because they are removed from the internet, at one point, paper wallets were considered to be more secure than other forms of cryptocurrency storage because of their air gapped nature.
Recently, Paper wallets have seen a significant drop in their usage in the recent past. Reasons for the drop in usage surround mainly because of their private key storage being in plain text and physical nature. This can lead to loss and theft of the same. The way you secure them is similar to securing your seed phrase that we will talk about later in the Seed Phrase preservation section.

A Software Wallet is a form of cryptocurrency wallet that’s based on software, so installed as a mobile app or accessed via a website, or installed as software on a desktop or laptop computer. The software itself stores your private keys that are used to access your cryptocurrency funds.
Software wallets, recently, Software-based wallets, also known as Hot wallet, are more accessible and more convenient therefore are the most commonly used wallets. Most common examples of software wallets are Metamask( Extension-based) , Electrum( Desktop-based) & Rainbow( Mobile-based). Software wallets are amazing because of their ability to connect to the blockchain and the Dapps. But the connectivity also opens up ways for malicious actors to compromise your security.
Software wallets store your private keys in your computer using encryption which might or might not generate encryption entropy using your password. This brings about a security concern because of the desktop being internet connected, anyone getting access to your desktop physically or virtually can potentially reach to your software wallet data file and steal your keys.
Hardware wallets are a form of offline storage. A hardware wallet, also known as Cold Wallet, is a cryptocurrency wallet that stores the user’s private keys (a critical piece of information used to authorize outgoing transactions on the blockchain network) in a secure hardware device.
Hardware wallets till date have been the safest way for individuals to store their cryptocurrencies. Because a hardware wallet stores keys in an offline manner. That makes it difficult to access by the attackers.
Hardware wallets should be used for low velocity asset holds. For high velocity trades, maintain balance in software wallets or transfer to Software wallet for trades. Once trade is done, transfer your funds back to your hardware wallet, that way you will protect your funds from future potential smart contract exploits. While keeping your hardware wallets like a true cold wallet.
Hardware wallets are considered the safest so far because they store your private keys in a secured offline environment, which never connects to the internet. Hardware wallets usually contain a secure internal chip like ATECC608A which are responsible to keep your private keys secure. The private keys never leave this chip even when you transact with your wallet. Even though hardware wallets have been hacked before as well, they are ways to improve its security model even further. More on that in the later sections.
Classify your Wallets:Best way to protect your wallet from Web3 connection scams is by never connecting your wallets to any web3 websites and Smart contracts. But how do you interact with smart contracts by never giving them any permissions to interact with your funds? Answer: Have multiple wallets. Classify each of them as follows:
Cold Wallet:Cold Wallet is a way to hold your keys in a completely offline manner. This is the wallet you want to use to hold the majority of your funds. If you do not still have a Hardware Wallet, you can create a software wallet and never create any sort of website or smart contract connection. That way, even though you could be attacked with phishing attack but will be safe from malicious websites and SCs.
This is the wallet meant for SECURITY.Hot Wallet:Hot software wallet is the one you want to connect to your trusted smart contracts. No non-trusted contract or less-trusted interaction should go through this wallet. This is the wallet you will be using most frequently for your DeFi ,metaverse and NFT interactions. So, all your high velocity funds will be living in this wallet.
This is the wallet meant for CONVENIENCE.
Burner Wallet:Okay so, you won’t be using your cold and hot wallet to carry out your experiments. So, how will you be executing your new Dapp tests and airdrop hunts? This is exactly where burner wallets fit in your security stack. Burner wallets can be created using software and hardware wallets. All your non-trusted and less-trusted activities happen with this wallet. Burn your burner wallet every couple months, it’s as simple as deleting your wallet from your metamask. Just make sure to transfer your funds, if any, from your burner wallet to another wallet before you bid adieu to it forever.
This is the wallet meant for CURIOSITY.
Smart Contract Security
Smart contract based Dapps sit over blockchains and need some kind of communication and permissions from the wallets, in order to execute a command. These commands can be deducting funds from the wallet to swap with another asset. But while there are many legit contracts, there is a threat to security if you grant permission to a malicious contract. So, it becomes important to know how to identify malicious contracts.
- Check code verification on Blockchain scanner
Check blockchain scanner like Ethscan, Bscscan, etc. If code is not verified, you’re probably dealing with a scam.
- Check Blockchain Scanner Comments section
If there are other users who have been scammed by a scam contract, it is likely they would’ve commented under the contract address about being scammed.
- Check for Token address authenticity
If it is a token, search for the token name or address in Google, CoinGecko, Unicrypt, Token Sniffer, BSC Check and DappRadar.
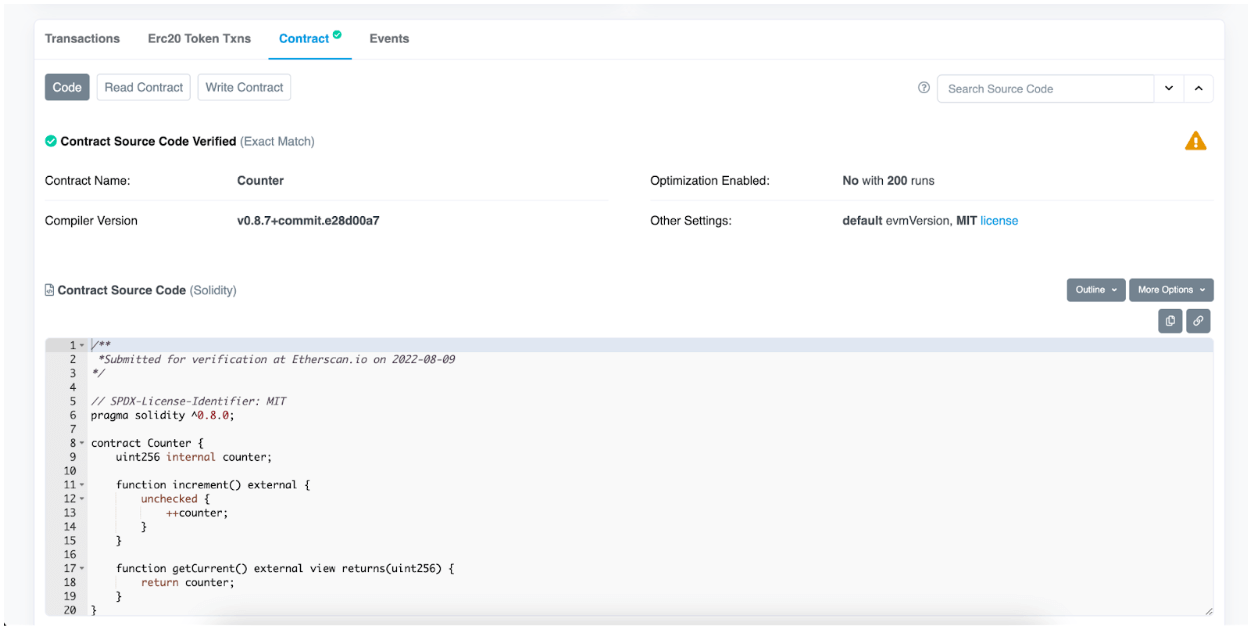
Maintaining wallets can be hard and sometimes you are needed to make connections because of fund unavailability or high gas fees. This raises the threat level of wallet towards future potential exploits relating to that smart contract.
For such cases, use smart contract revokers to browse all permissions granted to various smart contracts and revoke permissions in case you find a contract having unsafe permissions.
Securing Seed phrase
Seed Phrases are the biggest Single-Point-of-Failure in crypto security stack. Many investors have lost billions of dollars worth of crypto because of the loss or theft of their seed phrases. Back in 2017, Blockchain analysis firm chainalysis estimated that 23% of all Bitcoin in circulation could have been lost forever, already.
Online Backup
While many methods to store crypto have been experimented with, one method
that is strictly discouraged is storing your seed phrases online. Online backups
are readily available in the vicinity of the attackers with high surface area to
be attacked.
Offline methods include paper and steel backups. Both solutions come in Plain-text which widens the attack surface area, as anyone seeing the plaintext seed phrase can drain all your wallet at his disposal.
It is highly recommended to follow the experts guidelines while building security around your seed phrase storage. Some of them include
Gordian SeedTool iOS app (good UX but not air gapped)
- LetheKit
Glacier Protocol ( Bitcoin Specific )
- Seed XOR
Seedtool-cli ( air gapped PC )
But some of them tend to be too complex for the average user to implement, or may require you to buy a completely new set of networks and computers to build a secure environment. This can be especially tricky because any mistake while setting up a DYOR security stack can lead to permanent loss of funds. While there seems to be no better option securely to backup your Seedphrase. Seedless Wallets have come as a long awaited solution.
Most bitcoin wallets ask users to write down a recovery seed and keep it secure when you set up the wallet for the first time. But if mistakes are made, a recovery seed can make a wallet less secure, since the seed can be used to clone the wallet.
In the recent past, Seedless wallets have been in rising popularity. Seedless wallets replace the need to write down a backup passphrase and keep it secure. They do away with the hassle and stress of hodling your seed phrase in an unsafe way, thereby, removing any single-point-of-failure within crypto backups and improving overall security.
We at Cypherock believe in a Seedless future . Cypherock X1 empowers users to protect their keys by sharding wallet keys to 5 shards(One X1 Vault & Four X1 Cards), user needs only 2 of the 5 shards in order to reconstruct the Keys and manage their funds. Shards are stored in a way that no single shard gives information about other shards. This process completely takes away the single point of failure nature of seed phrases. As you can manage your funds even if you lose 3 of the 5 shards that too without ever worrying about anyone being able to read your seed phrase. Since your private keys are decentralized with Cypherock, it is 10x more secure than any other hardware wallet in the market and hence it is not exposed to the attack vectors with the current hardware wallets.
Recommended Writers to follow for Security
This is an evolving article and will be updated frequently to keep up with any new security development in the crypto security stack. If you believe you can add value to this article, you can email us at naman@cypherock.com
Connect with us:
Twitter :twitter.com/CypherockWallet
Telegram: t.me/cypherock

