

In the world of cryptocurrencies, safeguarding your digital assets is a top priority. The choice of tools to oversee your cryptocurrency holdings can make the difference between maintaining security or being susceptible to ongoing risks like hacking and malicious attacks. This article delves into the intricate world of cryptocurrency transactions, highlighting a critical vulnerability that could jeopardize your financial security. Imagine conducting cryptocurrency transactions blindfolded, leaving you exposed to potential attacks that could drain your digital wealth. In this blog, we explore the pivotal role of having a display in your hardware wallet to protect your crypto assets.
When you initiate a cryptocurrency transaction, whether it’s sending funds to a friend or conducting any operation, a series of exchanges occur between your computer (the host) running your wallet’s companion app and your hardware wallet. This is precisely what transpires when you endeavor to send cryptocurrency to a friend: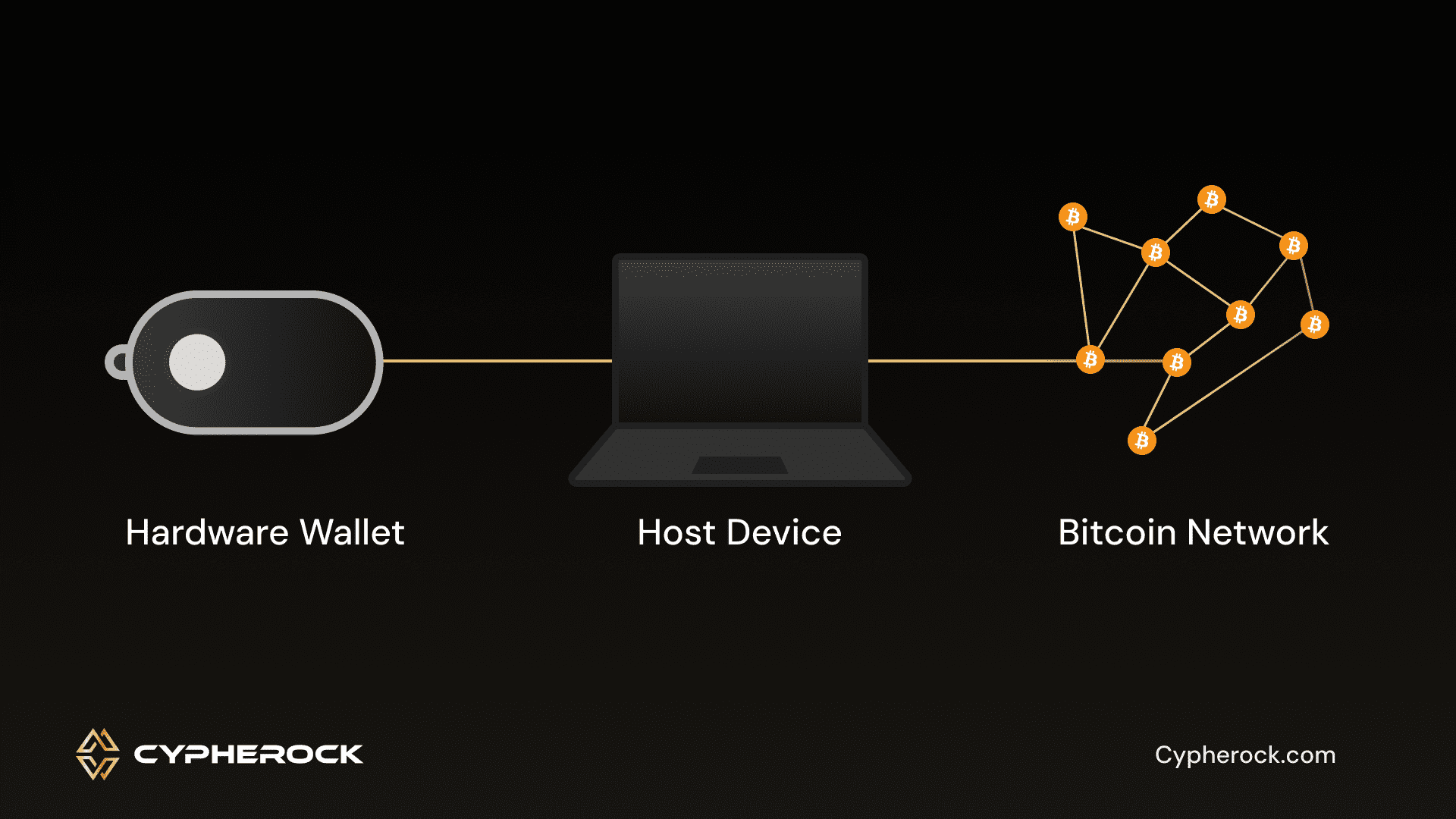
Imagine you’re using a wallet like Tangem (or any other wallet which doesn’t have a display), which lacks a display. In this scenario, once you input all the transaction details into the app, you simply tap your Tangem card to sign and confirm the transaction. This sounds very convenient, but yet, here lies the problem.
It’s conceivable for a relatively skilled attacker to compromise or hack the Tangem app. This opens the door to a slew of malicious attacks, including spoofing, phishing, and social engineering attacks. When the host (the companion app or the system running it) is compromised, the attacker can manipulate recipient addresses, change addresses, and transaction amounts initially entered by the user. The hacker can deceive the user into approving a fraudulent transaction by showing the same address and amount on the app but he internally alters the address and amount to his wish before the user signs it. Once this manipulated transaction is broadcast to the blockchain, all of the user’s funds are lost. A compromised host can display totally different transaction details.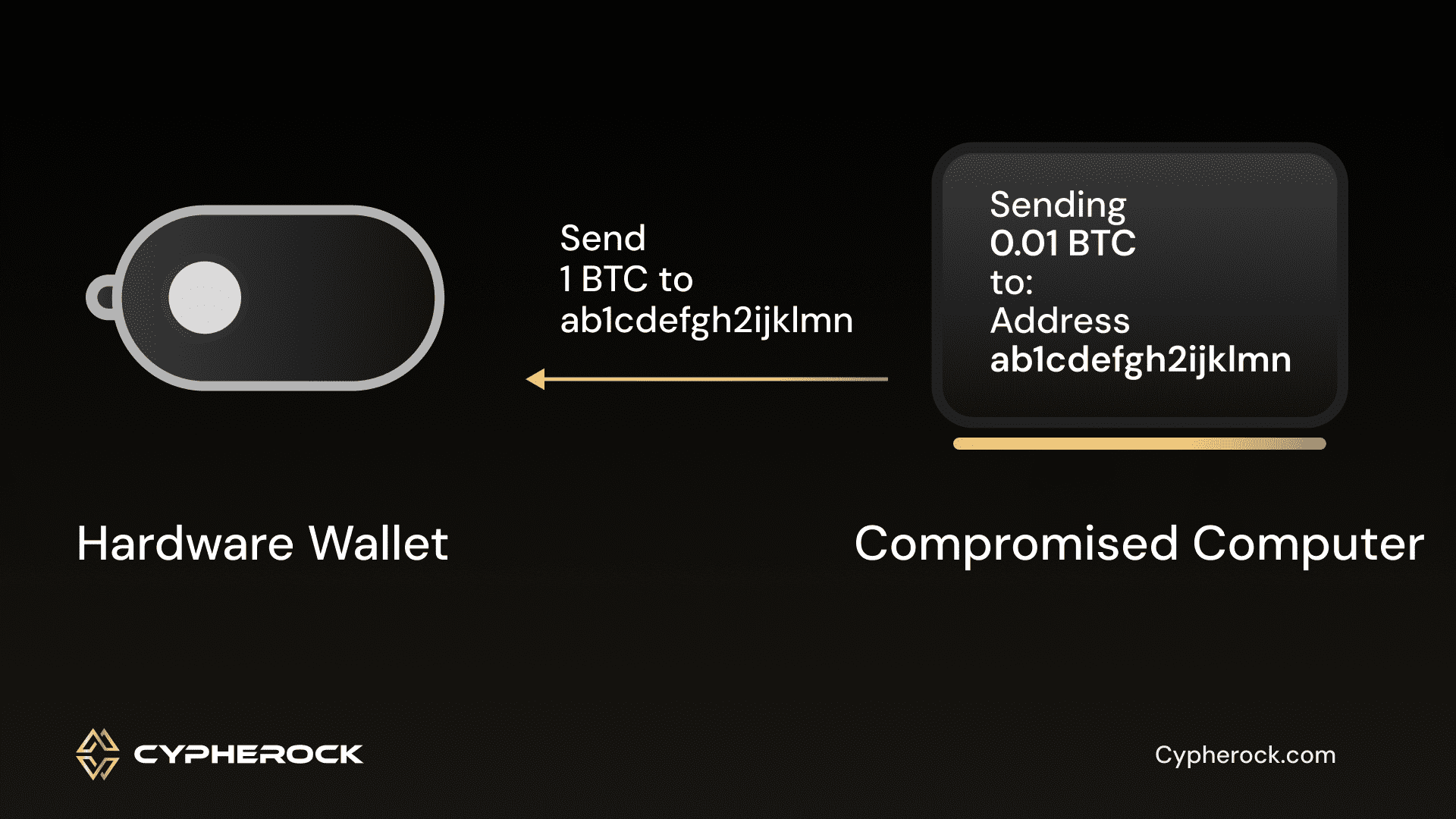
When users trust the host blindly and confirm transactions without visually verifying all the details on an offline display, they put their funds at risk. They may unwittingly send their precious assets to an address they never intended to use. For example, consider a scenario where you intended to send cryptocurrency to a friend, only to discover that all your funds have been dispatched to an account under the control of a malicious attacker or hacker. To avoid this pitfall, it’s crucial to manually scrutinize and validate all transaction details, including recipient addresses, coin types, and amounts.
Through social engineering tactics, attackers manipulate and trick users into interacting with elements they shouldn’t engage with. This is achieved by creating a fake user interface (UI) to deceive the user into clicking on something they shouldn’t. These elements may be disguised as something else or even concealed within the UI of compromised apps, effectively coaxing users into unknowingly granting consent to malicious actions, downloading malware, or even disclosing sensitive credentials like PINs, passwords, and even seed phrases.
In fact, numerous users have fallen victim to substantial financial losses within the crypto space due to these spoofing attacks. The solution, however, lies within easy reach. By simply opting for a hardware wallet equipped with a trusted display, individuals can substantially bolster their defenses against these pernicious threats and fortify their cryptocurrency holdings.
A trusted display should directly communicate with the wallet’s microcontroller unit (MCU). The code driving this display should be open-source, enabling users to verify communication between the MCU and the display. This allows the users to verify the components and code for ensuring safety. Importantly, there should be no intermediary components, such as an IC (Integrated Circuit), acting as a black box that could manipulate or store data.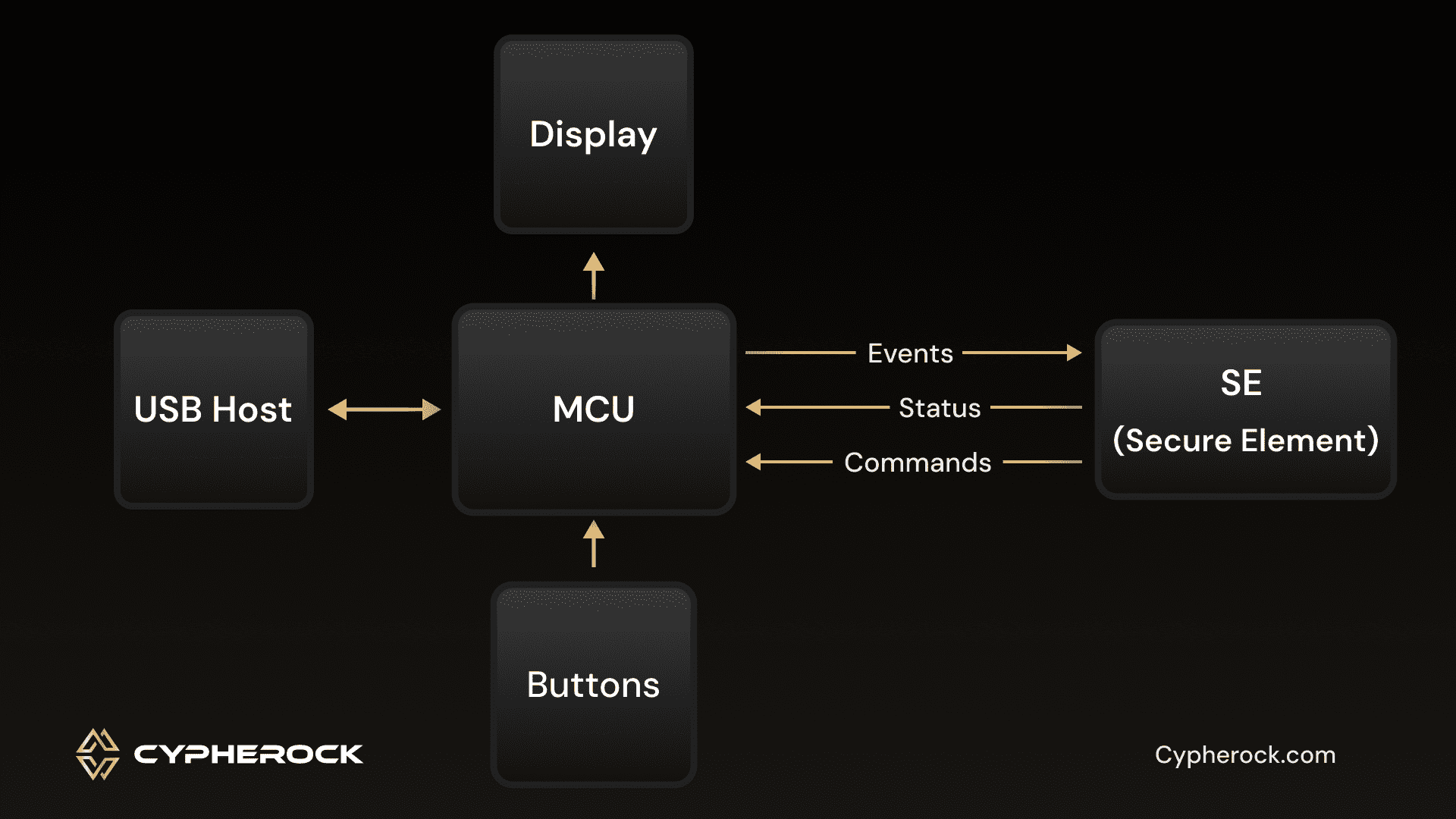
In practice, a trusted display provides users with all necessary transaction details, including addresses, coin types, and amounts. This empowers users to cross-check and verify this information against the companion app or host, reducing reliance on the host alone.
Because the hardware operates in isolation, it remains impervious to remote attacks initiated over the internet. This way no malicious attacker can hack the device and change what the display shows you, protecting against remote attacks.
Moreover, the trusted display serves as a secure means of verifying and confirming transactions. Acting as an intermediary between you and your cryptocurrency holdings, the trusted display allows you to visually review vital transaction details, including recipient addresses and coin amounts. Once the transaction data is presented, the wallet can prompt you for confirmation, typically through an on-device button press, before signing and transmitting the transaction back to the host device. This ensures that you can verify the accuracy of the transaction destination, reducing your reliance on the companion app or host.
It’s essential to acknowledge that no amount of security on the host device or the companion app can mitigate the fact that the hardware wallet has to trust the host device, if it cannot validate the transaction data independently.
The significance of a trusted display cannot be overstated. Removing the display from a hardware wallet undermines its security benefits. In fact, both Ledger and BitBox initially released hardware wallets (the original Ledger Nano / Ledger HW.1 and the original BitBox01 respectively) without displays but discontinued them due to complexities and security concerns.
In conclusion, while manufacturers may consider removing displays as a cost-saving measure, doing so compromises the security and integrity of hardware wallets. A trusted display is not merely an added feature; it’s a fundamental component that ensures users can protect their cryptocurrency holdings effectively. When selecting a hardware wallet, prioritizing one with a trusted display is a wise choice for those looking to secure their digital wealth with confidence.
We are live for orders @ www.cypherock.com/product/cypherock-x1
Connect with us:
Twitter: twitter.com/CypherockWallet
Telegram: t.me/cypherock
